Just like medieval castles, the best defense against any intrusion is one that is layered. ProStratus has adopted this approach to provide the highest level of cybersecurity for clients and their users.
ProStratus uses a variety of tools to protect a network environment. This includes protections at each level where breaches are possible.
The goal of the ProStratus approach is to make it difficult for a threat actor to use the same tactic to penetrate various elements of the network. For example, if a hacker is able to gain unauthorized access through the firewall, they will not be able to hide their network traffic footprint, nor will they be able to use the same method to penetrate host-based firewalls that are placed on workstations and servers.
ProStratus deploys firewall protection to protect against unwanted network penetration. We will work with you to configure access to allow for remote sessions through a Virtual Private Network (VPN) while protecting connections and data from unwanted observation or access.
ProStratus will monitor your network to detect unwanted or increased traffic, among other attack indicators.
ProStratus implements a robust End Point Protection system that includes personal firewalls on each workstation and server. This system is highly customizable with special permissions to allow for safe and secure remote access, as well as blacklisting programs and websites that are known threats.
ProStratus provides an active Security Operations Center (SOC) that will detect and mitigate known threats, including zero-day attacks, before they have the potential to impact the system. This helps ProStratus and clients to be able to identify legitimate threats that need to be immediately addressed.
ProStratus implements the policy of least privilege which limits the access of users to only the data that is necessary to complete their job.
This approach helps to mitigate the damage that is possible in the case of a data breach by limiting a threat actor to have access to a limited amount of corporate data.
This defensive philosophy also applies to applications and web access. Users are only allowed to access applications and websites that are approved by the client.
This approach allows for a greater level of detection of threat actors, as ProStratus can detect and be alerted about attempts that are made to access data, applications or websites that are not allowed by client policy.



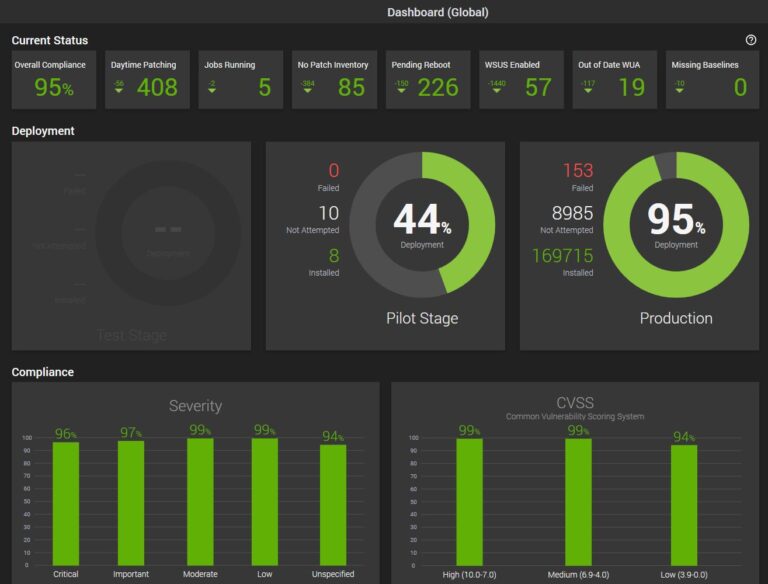
 Cyber-security live monitoring 24/7 - Detection and Monitoring - Analyze threats in real time
Cyber-security live monitoring 24/7 - Detection and Monitoring - Analyze threats in real time Network Operation Center - Certified Security IT Professionals - 24/7 Security Monitoring
Network Operation Center - Certified Security IT Professionals - 24/7 Security Monitoring Monitoring stolen credentials - Immediate notification of threats - Protect confidential customer records
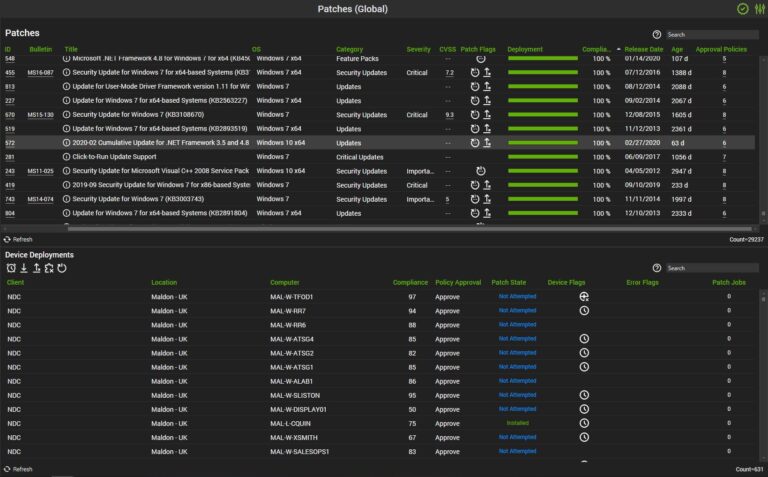
Monitoring stolen credentials - Immediate notification of threats - Protect confidential customer records Automatic patching on servers - Automatic patching on workstations - Security updates - Firewall management
Automatic patching on servers - Automatic patching on workstations - Security updates - Firewall management Web Filtering - Virus Protection - Malware, Spam, Spyware Protection - Automatic updates
Web Filtering - Virus Protection - Malware, Spam, Spyware Protection - Automatic updates Monthly security reports - Password management - Security risk score - Vulnerabilities & Threats - Action items and recommendations
Monthly security reports - Password management - Security risk score - Vulnerabilities & Threats - Action items and recommendations