Businesses of all sizes are increasingly aware of the importance of IT vulnerability risk management. After all, if your company is hacked, it can result in lost revenue, stolen data, and a damaged reputation. However, many businesses still struggle to manage their vulnerabilities effectively. The challenge is often rooted in the process. There is a lot of oversight and missteps from scanning and detection to impact analysis and remediation, which consumes a considerable chunk of an organization’s IT resources.
This blog post will discuss the top 8 barriers to effective vulnerability risk management and how to mitigate them.
What is Vulnerability Management?
But, first, here is a quick primer on the concept of vulnerability management.
Vulnerability management is the process of identifying, quantifying, and mitigating vulnerabilities in systems and applications. The goal is to reduce the risk of exploitation and data loss by ensuring that all known vulnerabilities are patched or otherwise mitigated.
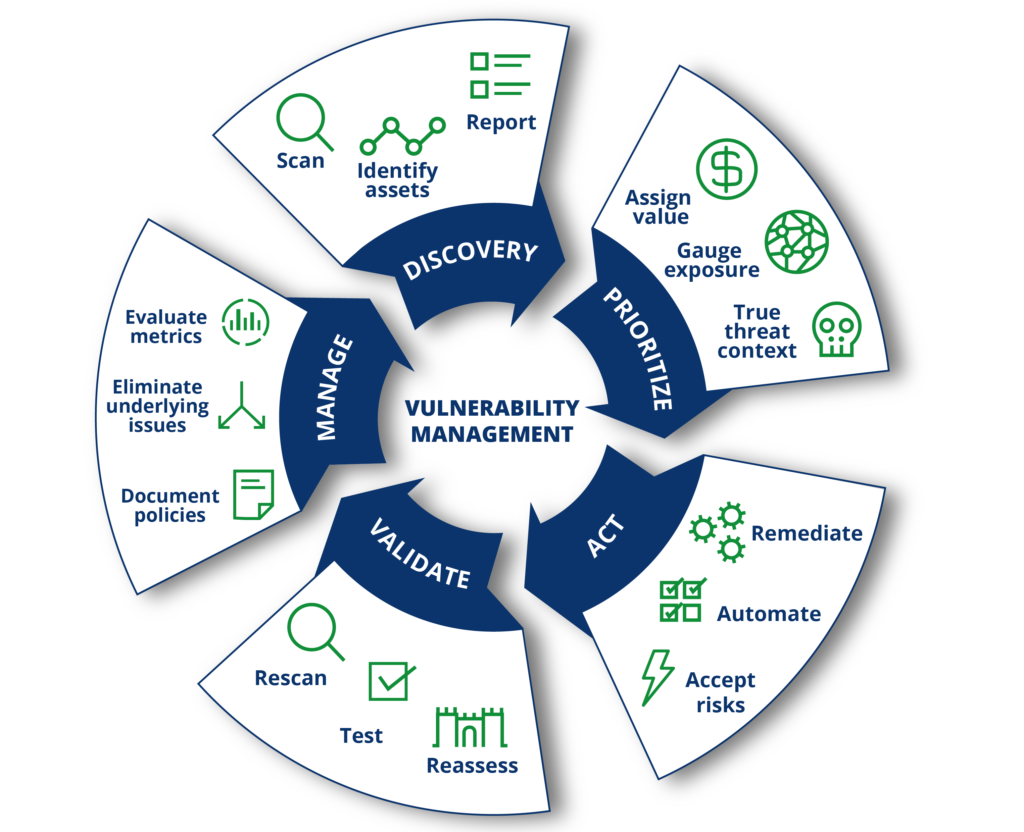
There are five key steps in vulnerability management:
- Assess: The first step is to assess the organization’s vulnerability landscape. Assessment includes identifying all systems and applications, scanning for vulnerabilities, and quantifying their severity.
- Prioritize: The next step is to prioritize the vulnerabilities. This involves ranking them according to their severity and likelihood of exploitation.
- Act: The third step is to take action to mitigate the vulnerabilities. This can involve patching, configuring security controls, or implementing workarounds.
- Reassess: The fourth step is to reassess the organization’s vulnerability landscape. This includes rescans and reevaluations to ensure that all vulnerabilities have been addressed.
- Improve: The fifth step is to improve the organization’s vulnerability management process. This includes streamlining workflows, automating tasks, and increasing transparency.
In today’s hyperconnected world and with the proliferation of technologies like 5G and the Internet of Things (IoT) and the adoption of remote working arrangements and digital transformation initiatives, vulnerability risk management has never been more critical. A recent report by IBM estimates the average cost of a single data breach at $4.24 million. The threat landscape is sophisticated and constantly evolving, which is why businesses need to have a robust and comprehensive vulnerability management program in place.
Below are the top 8 barriers with suggested solutions.
- Reactive Mindsets
Why are traditional vulnerability risk management systems failing in today’s world? Many enterprises concentrate on recovery instead of prevention. Taking a reactive approach, IT and security personnel put most of their efforts into repairing networks and minimizing harm after the fact.
However, while an overwhelming proportion of applications have security flaws, most problems are caused by setup mistakes rather than application code. Organizations must proactively discover and repair vulnerabilities that result from server misconfigurations, incorrect file settings, sample content, out-of-date software versions, and other factors linked to insecure deployment. Reactive measures aren’t enough; it’s time to put prevention ahead of reactivity.
- Lack of Dedicated Resources
Many businesses do not have a full-time staff member or team devoted to managing vulnerabilities. As a result, this critical task is often relegated to already overworked IT personnel who may not have the required skills or knowledge. In addition, they fail to invest in the latest vulnerability tools and software.
To effectively manage vulnerabilities, businesses need to have dedicated resources with the necessary skills and knowledge. They also need to invest in the latest tools and software.
- Inability To Assess The Full Impact Of Vulnerabilities
Many businesses fail to understand how a particular vulnerability could affect their business. For example, they may not know the potential consequences of an exploit or how much data could be compromised.
To make informed decisions about which vulnerabilities to patch and which ones pose the most significant risk, businesses need to assess the full impact of vulnerabilities. This again goes to investing in the right tools, software, and human expertise.
- A Constantly Changing Threat Landscape
The threat landscape constantly changes, making it difficult for businesses to keep up. Cybercriminals are always looking for new ways to exploit vulnerabilities in systems and applications. As a result, companies need to continuously update their vulnerability management program to ensure that they know the latest threats.
To keep up with the constantly changing threat landscape, enterprises should have a dedicated human resource responsible for monitoring and updating the vulnerability management program.
- Limited Expertise
One of the biggest barriers to effective vulnerability risk management is limited expertise. Many businesses do not have the necessary skills or knowledge to identify, assess, and mitigate vulnerabilities. To be successful, companies must hire the best. And, it doesn’t have to be expensive. Enterprises can now outsource many IT security processes to specialist firms that can better monitor and patch vulnerabilities.
- Delays In Patching And Remediation
Another issue is the cleanup process. Remediation of a security vulnerability typically takes roughly 200 days, according to a report by Whitehat Security. This laxity allows cyber attackers plenty of time to access the network and wreak havoc. Vulnerabilities that are deemed critical may go unpatched for months, if not years after they’ve been discovered and made public. That is, if they’re ever addressed.
When IT staff are blind to real-time dangers, they are inevitably reactionary. As a result, it is virtually impossible to prevent breaches and security incidents.
- Data Overload
Another big challenge for businesses is dealing with data overload. They may have too much data to sift through, or they may not have the right tools to analyze it effectively. As a result, they miss critical vulnerabilities that cybercriminals could exploit.
- Lack of a Formalized Process or Governance Framework
Many businesses do not have a set procedure for assessing, mitigating, and reporting vulnerabilities. This fact leads to confusion and chaos within the organization.
To effectively manage vulnerabilities, businesses need a formalized process or governance framework in place. This approach will help ensure that everyone is on the same page when dealing with security threats.
Getting Started With Vulnerability Risk Management
If your business wants to get started with vulnerability risk management, there are a few things you can do:
- Hire dedicated resources with the necessary skills and knowledge
- Invest in the latest tools and software
- Understand how vulnerable your business is and identify the most critical vulnerabilities
- Create a process or governance framework for managing vulnerabilities
- Regularly update your program to reflect the latest threats
IT Vulnerability Risk Management Conclusion
The bottom line is that businesses need to take vulnerability risk management seriously. By implementing these measures, they can protect their data and reduce the chances of being hacked. Cybersecurity should be a top priority for any organization.


